OAuth 2.0 is an authorization framework, which provides limited access to a particular service. For example consider that i need to call service and get some information, and the service provider wants to give me access only to a particular period to retrieve the data, in this kind of situation oauth2.0 provides a mechanism to access the service without providing any user related credentials to the service temporarily.
Note: Main reference for this article is the
https://tools.ietf.org/html/rfc6749?
Contents Included
1) Why OAuth 2.0
2) How OAuth 2.0 Works and Selecting the Authorization Grant
3) Usage in WSO2 APIM 2.1.0
4) Usage in WSO2 ESB 5.0.0
1) Why OAuth 2.0
Below figure illustrates how we normally used to access a service from our client application. In here you can see that we need to pass the services credentials to access the service. This will be an overhead because in that case we need to store the password and it may cause into security concerns and also if we want to revoke the access for the client then whole service password need to be changed.
Due to above mentioned disadvantages there was need for a protocol to handle the service invocation in a easier and secure way, that solution was OAuth 2.0.
2) How OAuth 2.0 Works
The basic request response flow in a OAuth 2.0 communication happens as below:
As mentioned in the above diagram the Authorization Grant call can be made in four types. We will look into each of them to get understand on the format of each calls.
Below is the Decision Tree which help us to identify which Grant Type to select when we are designing. The data has been extracted with the help of
https://auth0.com/docs/api-auth/which-oauth-flow-to-use
3) Usage in WSO2 APIM 2.1.0
Now we will move to the usage of this in WSO2 APIM 2.1.0. OOB WSO2 provides a Token API which helps us to generate tokens and get use of the above grant types supported by OAuth 2.0. WSO2 APIM 2.1.0 Token API supports below Grant Types.
- Authorization Code Grant
- NTLM Grant
- Password Grant
- SAML Extension Grant
- Client Credentials Grant
- Implicit Grant
- Kerberos OAuth2 Grant
- Refresh Token Grant
Authorization Code Grant
This is a type of grant we can use in a scenario where we have web application and it need to get permission to access a resource. Below flow diagram explains the implementation I'm going to take as use case.
In this grant we need to give two calls to retrieve the token.
1) To retrieve the Authorization Code
2) To Retrieve the Access Token
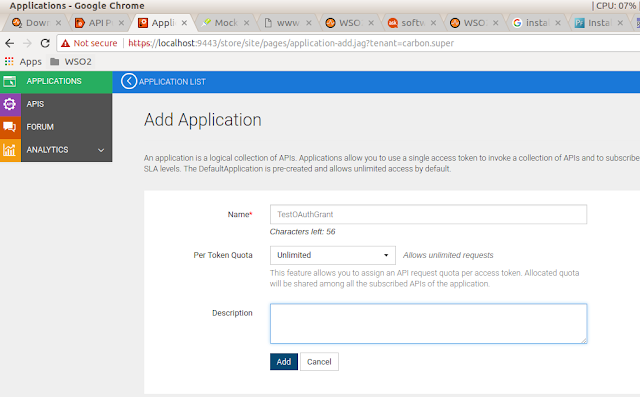
To continue on this, first we will create a API and a Application in APIM. Follow the below screen shots to achieve this.
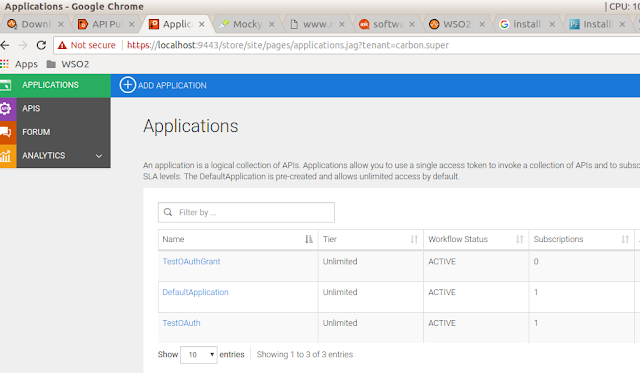
Now we have created the API. The next is to create an Application and subscribe the API to the Application. To achieve that log into store and below the below screens.
Now we have successfully configured and created the API. Now we need to create a web application to call and get the Authorization Code.
Below is a sample PHP Code to make the Authorization Code Request.
<?php
define("CALLBACK_URL", "http://localhost:80/ouath_call.php");
define("AUTH_URL", "https://localhost:8243/authorize");
define("CLIENT_ID", "gcKoevfZ4_ocYzvyZzBrkma7wpIa");
define("CLIENT_SECRET", "y1_yIcfxw6uaiDpJ2Mx1M1zfukca");
define("SCOPE", "PRODUCTION");
echo "Calling the Authorization Server to get the Authorization Code...";
$url = AUTH_URL."?"
."response_type=code"
."&client_id=". urlencode(CLIENT_ID)
."&scope=". urlencode(SCOPE)
."&redirect_uri=". urlencode(CALLBACK_URL)
;
echo "Authorization Request: " . $url;
header("Location: " . $url);
?>
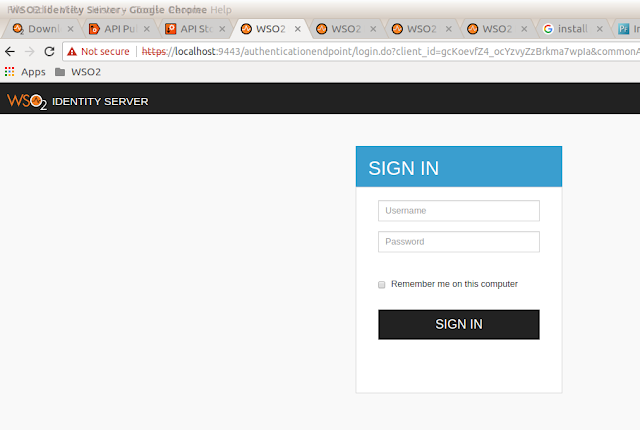
Go to http://localhost:80/ouath_call.php, once you done that you will see the below page get routed.
To Make the token request use the below PHP code segment. Here the AUTH_CODE is extracted from the response of the previous call which generate the Authorization Code.
<?php
define("CALLBACK_URL", "http://localhost/ouath_call.php");
define("AUTH_URL", "https://localhost:8243/authorize");
define("CLIENT_ID", "gcKoevfZ4_ocYzvyZzBrkma7wpIa");
define("CLIENT_SECRET", "y1_yIcfxw6uaiDpJ2Mx1M1zfukca");
define("SCOPE", "PRODUCTION");
define("TOKEN_URL", "https://localhost:8243/oauth2/token");
define("AUTH_CODE", "d1a687a2-0c97-31a5-a628-7ffad6b75009");
echo "Calling the Token API to get the Access Code...<br/><br/>";
$authorization = base64_encode(CLIENT_ID . ":" . CLIENT_SECRET);
$header = array("Authorization: Basic {$authorization}","Content-Type: application/x-www-form-urlencoded");
$content = "grant_type=authorization_code&code=".AUTH_CODE."&redirect_uri=".CALLBACK_URL;
$token_url = "https://localhost:8243/token" ;
$curl = curl_init();
curl_setopt_array($curl, array(
CURLOPT_URL => $token_url,
CURLOPT_HTTPHEADER => $header,
CURLOPT_SSL_VERIFYPEER => false,
CURLOPT_RETURNTRANSFER => true,
CURLOPT_POST => true,
CURLOPT_POSTFIELDS => $content
));
$response = curl_exec($curl);
curl_close($curl);
echo "Response" . $response;
?>
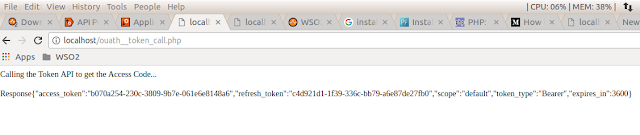
Once we make the call, we will get the below response with the Access Token.
Hope Authorization Grant explanation is useful and will continue the other contents in my next blog.